Zero Trust vs. VPN: Choosing the Right Security Approach for Your Organization

As businesses continue to rely more on digital communication and remote work, the need for secure access to sensitive information and systems has become increasingly important. This has led to the rise of two popular security frameworks: Zero Trust and VPN. While both approaches aim to provide secure access, they differ in their underlying philosophies and implementation. In this article, we'll explore the differences between Zero Trust and VPN and which approach may be better suited for your organization's needs.
What is Zero Trust?
Zero Trust is a security framework that assumes that no user, device, or network is inherently trustworthy. Instead, it requires constant verification and validation of users and devices before granting access to sensitive resources. In a Zero Trust model, access is granted on a "need-to-know" basis, meaning that users only have access to the specific resources they need to perform their job functions.
The Zero Trust approach involves several key principles, including:
- Continuous authentication: This involves verifying the identity and security posture of users and devices before granting access.
- Least privilege: Users are only granted access to the resources they need to perform their job functions.
- Micro-segmentation: Network resources are divided into smaller, more manageable segments, with access controls placed at each segment.
- Data encryption: Data is encrypted both in transit and at rest to protect against unauthorized access.
What is a VPN?
A Virtual Private Network (VPN) is a secure connection between a user's device and a private network, such as a company's internal network. VPNs are designed to provide secure access to resources and information while a user is outside the corporate network. When a user connects to a VPN, their traffic is encrypted and routed through a secure tunnel to the private network.
VPNs typically require users to authenticate themselves with a username and password, and some may also require a two-factor authentication (2FA) method. Once connected, the user has access to resources on the private network as if they were physically located within the organization's premises.
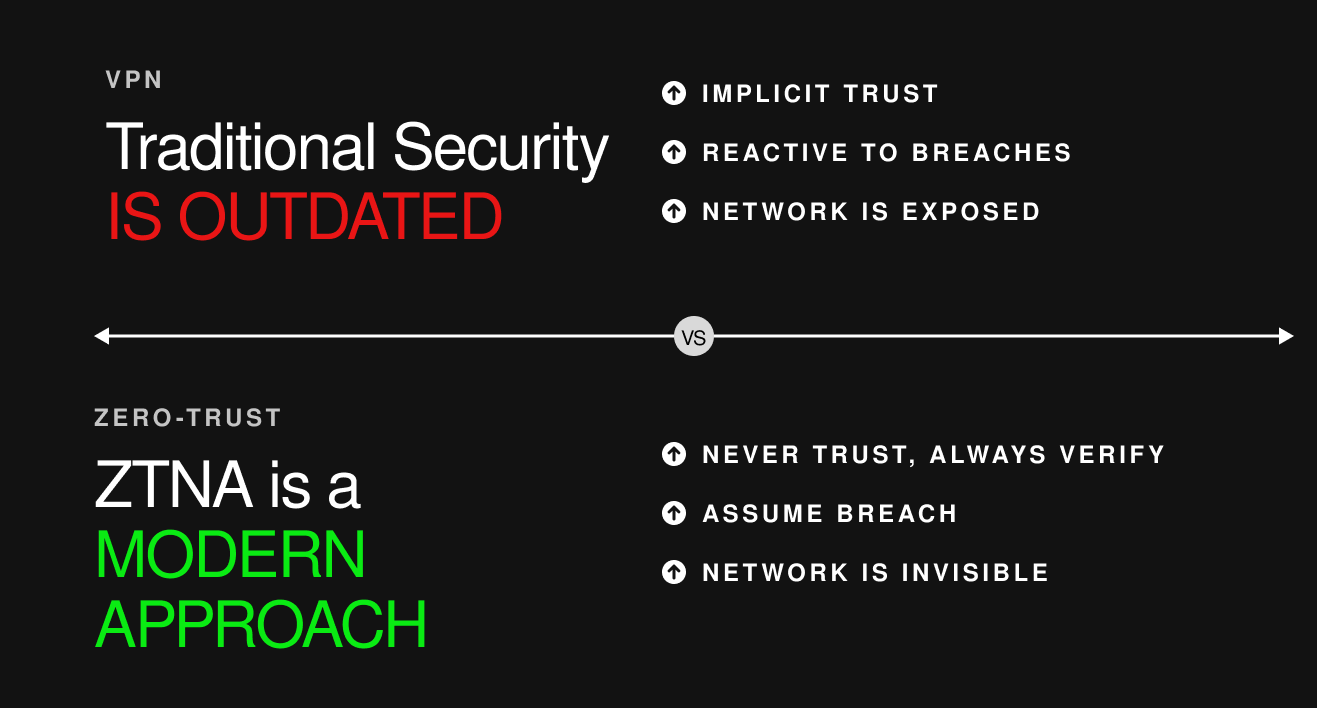
VPN vs. Zero Trust
While both VPN and Zero Trust aim to provide secure access to sensitive resources, they differ in their underlying philosophies and implementation. VPNs are based on the idea of creating a secure tunnel between a user's device and the corporate network. This approach assumes that once a user is authenticated and connected to the VPN, they are trusted and have full access to the resources on the network.
On the other hand, Zero Trust assumes that no user, device, or network is inherently trustworthy. It requires constant verification and validation of users and devices before granting access to sensitive resources. This approach is more granular and dynamic, allowing organizations to limit access to resources based on factors such as the user's role, location, and security posture.
Which approach is right for you?
The choice between Zero Trust and VPN ultimately depends on your organization's specific security needs and risk tolerance. VPNs may be a good option for organizations that need to provide remote access to a large number of users quickly and easily. However, VPNs can be vulnerable to security risks such as credential theft, man-in-the-middle attacks, and malware infections.
Zero Trust, on the other hand, provides a more granular approach to security that can help protect against these types of attacks. However, implementing a Zero Trust model can be complex and requires a significant investment in resources, including personnel and technology.
In conclusion, both Zero Trust and VPN can provide secure access to sensitive resources. The choice between the two depends on your organization's specific needs, risk tolerance, and available resources. Organizations that prioritize security and are willing to invest the necessary resources may find that a Zero Trust approach is the most effective way to protect their data and systems.